Use digital rights management and encryption
Encryption or digital rights management technology (DRM) can be used to control access to information. This is different from access restrictions placed on records when or after they're captured.
DRM and encryption may be beneficial when information is highly confidential, or if intellectual property is involved, but risks accompany their use. Read on to find out how to manage these risks.
Digital rights management
What is digital rights management?
DRM is usually part of the software or technology used to create information (e.g. using the password protection tool in MS Word to restrict access to a document).
It works by applying rules to information you create, such as:
- who can view, modify, print, copy, forward, and/or save
- when usage/access rights expire
- automatic deletion dates.
DRM restrictions are attached to records and remain attached no matter where you move the information or what you do with it. This differs from restrictions placed on a record once it's in a system, which allow you to move or change the record.
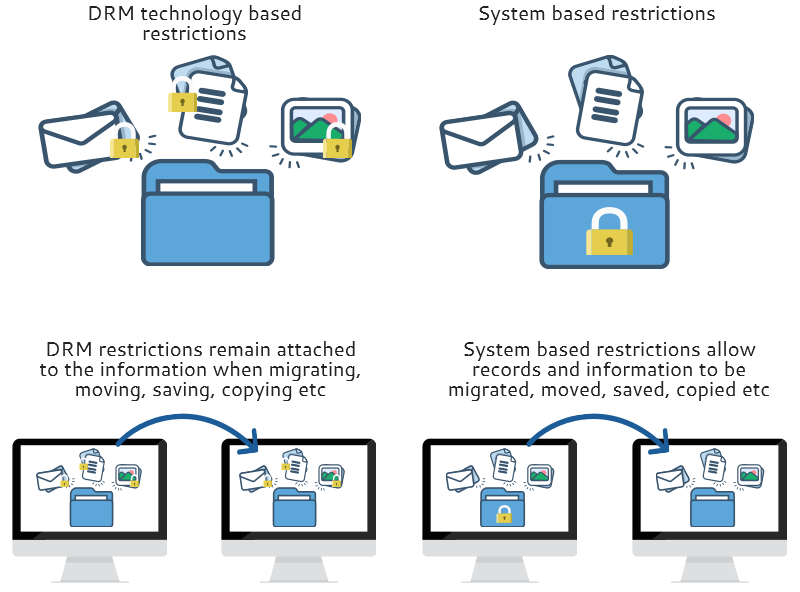
It is difficult to determine if DRM restrictions have been placed on a document as there is no global technical standard. Some programs will tell you depending on the restriction and the file.
Note: If intellectual property is involved, see the Creative Commons Australia to allocate and understand the legally permitted uses of information products.
Encryption
Encryption can protect information when storing or transferring records between different network environments or devices.
It is not a long-term solution for restricting access to or protecting information due to its level of risk.
You must manage encrypted records to ensure their ongoing readability.
You should document the encryption and decryption of records under appropriate security controls, and carefully manage the required decryption keys and certificates.
Note: Digital rights management controlled information is usually encrypted.
Risks to records
Certain features of DRM technologies and encryption increase the risks to records.
Expiration dates/auto-deletion
- Early disposal of records may occur when the expiration rule conflicts with the relevant retention period.
Auto-deletion
- Disposal of records may occur without considering their value beyond the prescribed retention period. Setting up an automatic deletion may mean records still required for business or legal purposes are inadvertently lost.
- Some eDRMS won't allow records controlled by DRM to be deleted.
- Required information and metadata about the destruction of records may not be captured.
Print disabling
- Some DRMs restrict or disable printing, which can affect how you keep records (e.g. if you have to keep it as a paper record).
Prohibition of saving/ forwarding
- You may be unable to capture and keep a record if forwarding or saving is restricted.
- Some eDRMS won't allow you to capture records controlled by DRM, or restrict actions like deleting or accessing.
Prohibition of viewing
- Records need to be accessible not just to the agency that created them, but also to other agencies, organisations and people (e.g. the audit office, RTI requests, legal proceedings). If access has been restricted using DRM, you may not be able to access or provide access to the required information.
Prohibition of copying/modifying/saving
- Management and preservation of records may be restricted. If digital records are not preserved, they may not remain accessible for the full retention period.
- Usability of records may be restricted, particularly if situations change, functions or activities are outsourced, or if a machinery-of-government change occurs. You need to ensure that records remain usable and accessible for as long as required, regardless of where the records are located or who is responsible for them.
- Your ability to re-use information may be reduced. For example, copying or using information to create a new document may not be possible if restrictions have been applied to the original version.
Encryption
- Records may become inaccessible, unreadable or lost if the encryption and decryption process is not appropriately managed, or if the keys and certificates required to decrypt the information are lost.
Remote attestation
- Remote attestation means that each time protected information is accessed, there is communication between the DRM system and external servers. Personal data is at risk of being collected by the external server, and that information may not be stored securely or appropriately managed. The collection and use of information must be consistent with the Queensland Government privacy requirements, and explicitly supported through contractual agreements.
- Access can be compromised if the DRM technology needs to communicate with an external server to verify access restrictions or rules. This connection to an external server may also affect how and when you can access the record and how you can use it.
Use DRM and encryption
Before using encryption or DRM technology, you should:
- assess the need to encrypt records or use DRM technologies based on records' security classification and type, and the business requirements
- look at how the record may need to be used now and in the future, including access, preservation, right to information requests, auditing, legal purposes
- think about alternative methods–this depends on how much the record is used, how long you need to keep it and the available safeguards (e.g. restricted access privileges, auditable events history checks, activity logs and network firewalls)
If you are going to use DRM or encryption, you will need to:
- assess the risks to records and the business
- ensure DRM restrictions or encryption is removed before capturing records
- put strategies in place to minimise risks and ensure that your agency's records can be kept for as long as necessary
- include a process for identifying, treating, capturing and managing records that have been encrypted or had DRM restrictions applied
- consider the information access requirements and how you would ensure records remain accessible for as long as they need to be kept
- develop a documented position on accepted scope and use of the technology
- decide who can use the technology (i.e. who can have software installed)–you might be able to link it to your agency's staff directory to limit the use of DRM to specific groups or people
- decide what records the technology can't be used for (e.g. high-risk/high-value records)
- maintain formal encryption/decryption key or password management regimes
- only store security classified information in encrypted form or with DRM restrictions applied for as long as that level of security is required, then decrypt the information/remove the restrictions for subsequent storage.
Note: Check the technologies you use for DRM technology and whether it needs to be enabled or if it can be disabled or configured for your agency.
More information
Find out more about using DRM technologies:
- State Records South Australia–Digital Rights Management–Implications for Recordkeeping (PDF, 78.3KB).
For more about security classifications and the use of encryption technologies in state government, refer to: